Every Android Device Since 2012 Impacted by Vulnerability
get hold of secrets stored in the device.
passwords, your personal photos, emails, instant messages
get hold of secrets stored in the device.
passwords, your personal photos, emails, instant messages
China could order its manufacturers to create backdoors for spying in their devices
https://www.wired.com/story/one-minute-attack-let-hackers-spoof-hotel-master-keys/
With a $300 Proxmark RFID card reading and writing tool, any expired keycard pulled from the trash of a target hotel
allowing anyone to take control of the ski lift’s operational settings.
https://www.wired.com/2016/08/oh-good-new-hack-can-unlock-100-million-volkswagens/
Wired:
IN 2013, WHEN University of Birmingham computer scientist Flavio Garcia and a team of researchers were preparing to reveal a vulnerability that allowed them to start the ignition of millions of Volkswagen cars and drive them off without a key, they were hit with a lawsuit that delayed the publication of their research for two years. But that experience doesn’t seem to have deterred Garcia and his colleagues from probing more of VW’s flaws: Now, a year after that hack was finally publicized, Garcia and a new team of researchers are back with another paper that shows how Volkswagen left not only its ignition vulnerable but the keyless entry system that unlocks the vehicle’s doors, too. And this time, they say, the flaw applies to practically every car Volkswagen has sold since 1995.
“It’s a bit worrying to see security techniques from the 1990s used in new vehicles,” says Garcia. “If we want to have secure, autonomous, interconnected vehicles, that has to change.”
Despite their dystopian appearance, the group’s six mining farms encompass eight petahashes per second of computing power, whose brute force as of October accounted for 3 percent of the entire Bitcoin network.
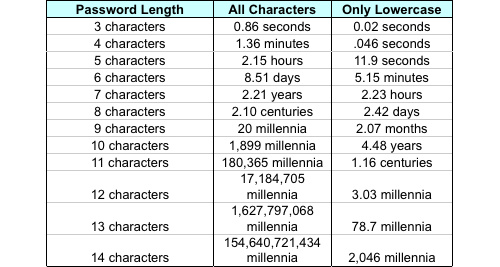
Randomly substitute numbers for letters that look similar. The letter ‘o’ becomes the number ‘0′, or even better an ‘@’ or ‘*’. (i.e. – m0d3ltf0rd… like modelTford)
Randomly throw in capital letters (i.e. – Mod3lTF0rd)
Think of something you were attached to when you were younger, but DON’T CHOOSE A PERSON’S NAME! Every name plus every word in the dictionary will fail under a simple brute force attack.
Maybe a place you loved, or a specific car, an attraction from a vacation, or a favorite restaurant?
You really need to have different username / password combinations for everything. Remember, the technique is to break into anything you access just to figure out your standard password, then compromise everything else. This doesn’t work if you don’t use the same password everywhere.
via lifehacker.com
Det er mellom 6 og 8 tegn det tar av for alvor. Du bør lese hele artikkelen. Og tenkt deg ekstra godt om på epost-passordet. Har en først kommet seg inn i innboksen så kan en få tilsendt nytt passord eller påminnelse fra de fleste andre steder.
via boingboing.net Ikke helt ny, men fremdeles interessant.